What is Encryption?
By Anagha Arvind
November 23, 2020
Any phone call you make, text message you send, item you purchase online, or bill you pay for, uses some form of encryption to protect your identity and maintain your privacy. The roots of encryption can be traced to ancient Greece where codes, or ciphers, were used to jumble numbers and letters on paper to encode information that was transferred between generals. As long as both parties had the proper cipher, they would understand the cryptographic message. Encryption and cryptology have evolved to be used by governments and militaries for centuries, especially in wars. Today’s encryption is completely computerized and has extended to everyday applications.
This article aims to tackle the following topics:
- What is Encryption and how does it work?
- Why is Encryption important?
- What are the types of Encryption?
- Encryption and the Law
- How can you improve your Encryption?
What is encryption and how does it work?
Encryption is an essential component of cybersecurity in which data is protected by encoding plain text into an unreadable, scrambled ciphertext. This is done using a confidential encryption key made with a specific algorithm, that can only be decoded by the recipients of the information with a corresponding decryption key. This digital data can include text messages, emails, health reports, and banking account information that can be transferred through networks, stored on computer systems or the cloud. The decryption key allows for the decoding of data by using more algorithms that unscramble ciphertext back into plain text. These encryption keys consist of random and unique sequences of numbers, which are created using random number and letter generator algorithms. For confidential information such as passwords and PIN numbers, a one-way cryptographic hash can be applied to the key to add more random sequences to the ciphertext, making it difficult to view the original text without the correct authentication. Truly secure encryption will ensure that a third party without a decryption key cannot decrypt the ciphertext through brute force, otherwise known as guessing.Why is encryption important?
A report from IDC and Seagate states that global data is expected to increase more than 5x, from 33 zettabytes (33 trillion gigabytes) to 175 zettabytes. As vast amounts of data are generated, transmitted and stored, occurrences of cybercrime and data breaches increase. The Identity Theft Resource Center reported that the number of US data breaches in 2019 increased by 17% from 2018. Data is at risk of leaks especially when in transit, which refers to data transfer between endpoints. New security threats are constantly emerging, increasing the prevalence of these leaks. Encryption allows for data to remain safe in storage devices like phones, hard drives and databases or in transit over servers and the Internet. Businesses have increasingly implemented encryption procedures to protect their consumer data from unauthorized agents and to develop trustworthy and secure relationships with their customers. Additionally, encryption avoids businesses having to pay expensive non-compliance penalties in the event of a data breach when regulations are violated. If you use the internet to file your taxes, make money transactions and conduct personal matters, it is important to use a website secured with encryption.What are a few types of encryption?
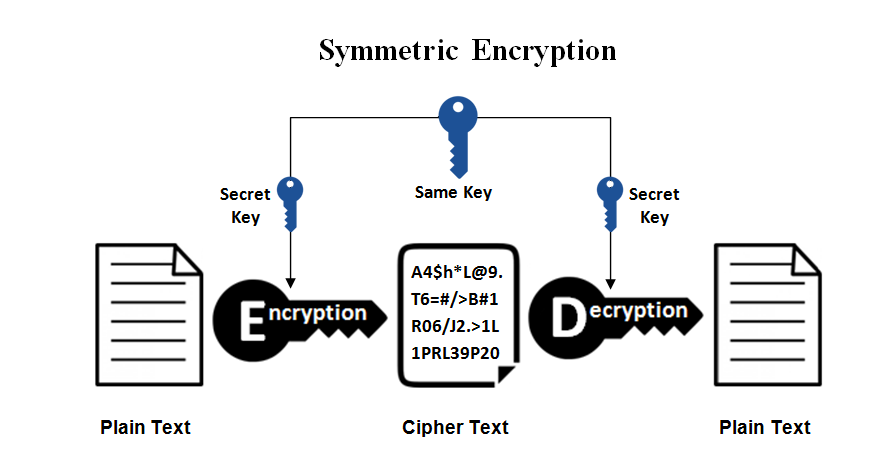
Source
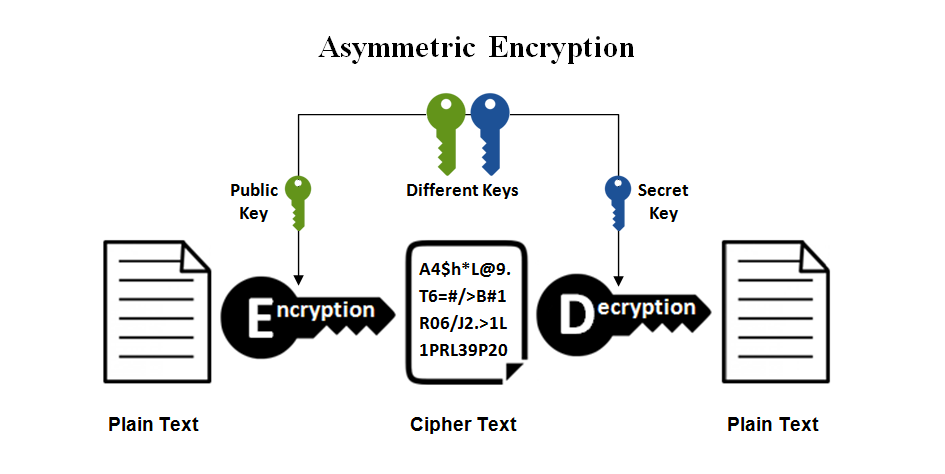
Source
There are two methods of encryption keys – symmetric and asymmetric – and all types of encryption fall under these two methods. The symmetric method has one secret key that encodes and one that decodes the information, usually applied to 1:1 sharing and small amounts of data. The asymmetric method uses a public key accessible to anyone to encrypt, and a private key accessible only to intended recipients to decrypt. The creation of public-key encryptions requires advanced computing, so many businesses resort to a combination of symmetric key and asymmetric key encryption. For example, two computers can be involved in data transmission in which one will create a symmetric key and send it to the other with a public key. These two computers maintain communication using the symmetric key that is completely private. At the end of the session, the symmetric key can be discarded and a new one would be created for a new session. Public key encryption is created from a secure hash algorithm and is an advanced version of the original ciphertext. It makes it almost impossible to recreate or access the original information without knowing the hashing algorithm.
Secure Sockets Layer (SSL) is a mechanism of encryption used by websites to protect sensitive user data by keeping HTTP requests and responses secure from attackers. Transport Layer Security (TLS) is the successor that has improved upon the characteristics of SSL and is, therefore, more secure. SSL and TLS are often used interchangeably. One can check if a website is encrypted by looking for a padlock symbol and an “https://” in the website address. This means any information transferred from you to the website is secure and only visible to the two parties involved – a server and a client. Digital SSL/TLS certificates allow websites to move from HTTP to HTTPS and act as the middleman between the server and client or between two computers, validate them and then provide the public key. The certificate is hosted by the visited website’s server and contains its domain name, public key and other relevant information. To be considered valid, domains need to obtain a certificate from a certificate authority (CA). When the browser sends a public key and certificate upon requesting a secure page, there are three protocols that are checked. (1) The certificate needs to come from a trusted third party CA, (2) it needs to be valid and (3) it has an established relationship with the website it is coming from. To create a secure connection with a website, the certificate verifies the identity of the site. If the values do not match, there will be a certificate error in the browser. Although you may still be able to proceed, it is advised not to provide sensitive information to the website.
Data Encryption Standard (DES) is a low-level encryption standard established in 1977 by the US government. While DES can offer 70 quadrillion combinations from a 56-bit key, brute force attacks can easily decrypt the data. An updated version deemed Advanced Encryption Standard (AES) was developed in 2001 and has become the most popular global encryption standard in protecting classified electronic data. The US government and organizations that collect Personally Identifiable Information (PII) like birthdates and Social Security Numbers have implemented AES in their programs, as the software and hardware are easy to handle while maintaining optimal security. Even consumers can encrypt their text messages with online AES web tools. AES has 128-, 192- and 256- bit keys which promise between 300,000,000,000,000,000,000,000,000,000,000,000 to 3,402,823,669,209,384,634,633,746,074,300,000,000,000,000,000,000,000,000,000,000,000,000 key combinations depending on the bit number of the key, and is therefore considered a sufficiently robust encryption option. For example, the 256-bit encryption makes it 340 billion-billion-billion-billion times harder to decrypt than the 128-bit.
Encryption and the Law
Some laws have mandated encryption to be applied to certain types of data. The Health Insurance Portability and Accountability Act (HIPAA) requires patient health care to be protected online, while the Family Education Rights and Privacy Act (FERPA) requires student records to be protected. Similarly, the Fair Credit Practices Act (FCPA) requires retail companies to protect consumer details. Encryption is a viable option to protect this information to stay compliant with these acts, otherwise, companies would have to pay fines.. There has been a two-decade-long ongoing argument between technologists, the government and law enforcement regarding the extent of encryption, specifically end-to-end encryption (E2EE). Regular encryption only protects data that is in transit between a client and a server and the service provider has access to the data as they have the decryption key. However, end to end encryption does not allow for the service provider to access the data as they do not own the decryption key. While privacy advocates want users to maintain confidential online communication without the threat of cyberattacks, some lawmakers believe there should be a way for authorized parties to be able to access this communication through a backdoor to prevent and investigate criminal activity and gain access to terrorists, traffickers and pedophiles. Privacy advocates and security experts support E2EE as they oppose government mass surveillance and argue that a back door could instead provide access to cybercriminals, terrorists and foreign hackers. The topic of EE2E gained popularity in 2013 after Edward Snowden leaked data from the NSA, therefore exposing how much personal and intelligence information government organizations have access to, through companies like Google and Facebook. Following this incident, Google and Facebook encrypted 80% of their web traffic to protect their user information. In a 2019 Guardian article, Edward Snowden continues to condemn the US government for undermining data protection through encryption, stating “…our public infrastructure and private lives will be rendered permanently unsafe”. Despite these arguments, more social media companies are incorporating EE2E in their messaging applications. For example, WhatsApp implemented EE2E to all types of messages and phone calls in April 2016. Thus, there has been an overall recognition of the importance of encryption for the protection of data, whether it be at a small scale for regular consumers or at a large scale involving organizations and governments.How can you improve your data security with encryption?
- Use messaging and calling services such as WhatsApp and Signal to conduct your communication. These apps provide E2EE and more privacy than email, phone calls and text messages. For example, Google has the ability to view your Gmail account, unless you choose to encrypt your emails and only if the other email provider allows TLS encryption. Social media platforms like Facebook and Zoom are slowly enabling EE2E in their services.
- Make sure to check for SSL or TLS encryption by looking for a padlock or “https” in the URL of the website, especially if you are entering personal information online. Try not to use websites that show a certificate error. Understand that any sensitive information is privy to cybercriminals and should therefore be encrypted.
- Encryption keys should be protected with memorable passwords for the user to access. If the user loses access to these keys, they could lose access to the data. Use a password generator and manager to develop complex passwords that you do not lose.
- Rotate encryption keys to defend against cyberattacks that use frequency analysis to study the frequency of letters and numbers occurring in ciphertext to decrypt the message. Although this was common with older, weaker forms of encryption and not prevalent with modern encryption, it is a good habit to follow. This is especially helpful in conjunction with applying multiple layers of encryption.


