The True Cost of Cybersecurity for Small and Medium Businesses
By Ryan M. Norchi
April 30, 2021
According to some estimations, the global cost of cyber attacks in a year could total up to about $1 trillion, over 1% of the global GDP. Such a high number should not be surprising to most readers. The modern age has seen the development of machines capable of tremendous computing power. The high monetary value of online data has attracted a great deal of that computing power for criminal activity. Cybercrime is likely going to continue to get worse in the future. That the cost of a cybersecurity breach runs high is no secret, but the exact price can be quite jarring. Despite the heavy potential losses, many business owners remain uninformed about the complexities of cybercrime. It is not uncommon for small and medium-sized business owners to assume that cybercriminals might only want to target larger corporations, or to underestimate the hidden costs of a cybersecurity breach. The true cost of a cyber attack goes well beyond balance sheets. In addition to that, of course, is the necessary cost of cybersecurity. Buying and maintaining strong security is only one of many best practices a business should utilize. But these practices are important to maintain on your own, as there is currently very little government-mandated regulation regarding the cybersecurity needs of businesses outside of a few key industries. The cost of a cyber attack is high, but with lax government regulation, it is important for owners of businesses of all sizes to maintain the best practices and guidelines laid out by the National Institute of Standards and Technology.
While it might appear to make sense that only large, clumsy companies flush with cash would be the targets of such high tech crimes, it is, as previously noted, equally important for small and medium-sized businesses to maintain cybersecurity standards as well. A survey conducted in 2012 by the National Cyber-Security Alliance found that about 71% of security breaches target small businesses. This creates a stark contrast to this survey from 2020 which reports that around 60% of small and medium businesses do not believe their company is likely to be targeted by cybercriminals. While larger companies provide a greater reward, cybercriminals are highly likely to increase their attacks on small and medium-sized businesses. This may seem counterintuitive, but small businesses spend less on cybersecurity and are less likely to have a dedicated IT department, or the man-hours necessary to go through the reporting process after an attack. This makes small businesses far easier to target than large ones, which are more likely to increase cybersecurity spending as cybercrime techniques are only going to become more advanced with time.
It is known that the global monetary cost of cyber attacks is quite large, but many business owners might wonder about the costs of a cyber attack that go beyond the cash that was stolen. The true hidden cost of cyber attacks also extends to opportunity costs in sales, marketing, and manpower. These costs can be far more difficult to quantify, but should not be forgotten. Typically, the discovery of a cyber-attack involves some amount of system downtime where a company’s technology does not work at maximum capacity. System downtime is one aspect of security hack recovery that leads to reduced efficiency for the company itself. For a period of time, employees are unable to work, opportunity costs will continue to mount, and the entire IT department might be focused on recovery when their attention may have been better put to use on other projects. Consider, also, that damage to one company tends to have a ripple effect throughout entire industries. when any business suffers from a cyber attack, other businesses will also suffer inefficiencies. For example, any company in the service industry that provides a service for other businesses will negatively affect those businesses if the IT system goes down. Total monetary damages to the company itself also include those suffered by branding and image damages should the public find out about any such breaches. This can lead to a loss of revenue and increased need for future marketing, potentially costing a cyber attack victim more than simply what was stolen. Then there are costs suffered after an attack. Cyber insurance costs may increase, and incident response costs continue long after the breach has been detected. These costs include compensation for clients whose data may have been stolen, as well as any necessary outside assistance from consultants or lawyers. Most small businesses are becoming more dependent on the internet over time, and this likely is not going to change, so it will always be important to remain aware of the potential costs of cybercrime that exist just as one might be aware of the potential costs of a home burglary.
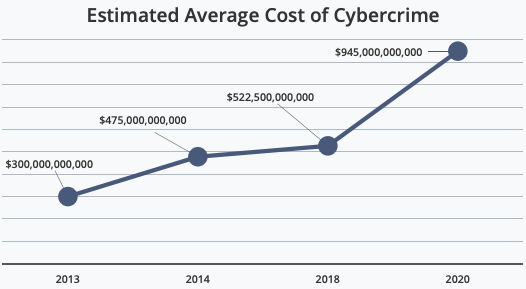
Cyber-security protocols are not widely mandated by the government. Despite some efforts and movement toward mass cybersecurity regulations in the United States that would help businesses stay safe, the only current government intervention for data security is localized to specific industries. The Health Insurance Portability and Accountability Act, (HIPAA), is the security rule that seeks to protect the privacy of health information. HIPAA establishes security standards for any organization holding certain health information of clients. The Gramm-Leach Bliley Act, (GLBA), fulfills a similar purpose for the financial industry. GLBA is intended to protect consumers by mandating that financial institutions safeguard clients’ data and inform them of any potential information sharing practices. Similarly, the Federal Information Security Modernization Act, (FISMA), is a regulation imposed on the government itself. FISMA was part of the homeland security act in 2002 and authorizes the Department of Homeland Security to oversee the implementation of security policies for various government agencies. These laws are a reasonable start. Healthcare, finance, and government information, in the wrong hands, can leave many people very vulnerable. However, until further laws are enacted, and existing ones are expanded, businesses will remain vulnerable to cybercrime.
While government bureaucracy may lag in terms of cybersecurity education and regulation, individuals can take measures to protect their own businesses. The Federal Communications Commission, (FCC), has a suggested list of best practices on their website for small business owners that might not have access to a large IT department. The FCC suggests training employees on basic security policies, maintaining high-quality security software and operating systems in conjunction with standard firewalls, having a backup plan that involves cell phones and hard copies of important data, having a secure Wi-Fi network, staying safe with regard to company credit cards and other financial tools, and ensuring that physical access to computers as well as online access to accounts is secured through the use of passwords and authentication. There are many ways for small businesses in the United States to increase their cybersecurity levels, but these guidelines set forth by the FCC are a good place to start.
Cybersecurity implementation is a must for any business that wants to operate in the modern age. As cybersecurity technology advances, however, so do cybercrime tactics. Small and medium-sized businesses remain the most vulnerable. Not only do they often lack the resources and IT strength that big businesses have, but the loss of clients and efficiency are damages that smaller businesses sometimes cannot handle. Despite being vulnerable, and targeted often by hackers, many small business owners still do not take the important precautions necessary to safeguard against such attacks. Given the potential cost and loss of business threat posed by cybersecurity breaches, it is important that, until stricter government regulations are passed requiring increased cybersecurity protocols and making education on the topic easier, business owners take the initiative to educate themselves further on the importance of cybersecurity, and potential options worth exploring. Human-id is one potential measure with which small businesses can increase their security without incurring great costs. The Human-id blog also offers articles on how SMEs can bolster their cybersecurity, data leak prevention, and mitigation of other business risks; important resources for any small business seeking cost-efficient ways to buff security.


