Should you use email or phone number authentication?
By Helena Miller
August 9, 2021
Email authentication and phone number authentication are two widely used authentication methods that are said to protect people from hackers and other cybercriminals; but, they potentially make it easier for cybercriminals to invade user privacy and protection. While it appears that they make the process of logging into accounts and applications easier, oftentimes, they can be used for fraudulent and harmful functions. Some downsides include data leaking, stealing, and hacking. While both methods have their advantages and disadvantages, phone number authentication has been proven to be more useful to protect personal information than email authentication.
What is email authentication?
E-mail authentication is a technological method that enables people to establish that an email is from who it says it is from. It can refer to the use of email as logins, and its primary purpose is to end negative and fraudulent uses of email like phishing and spam. Examples of email authentication that aim to restore integrity online are SPF, DKIM, and DMARC.
To start, an email login is a type of login that uses someone’s email address to access a website or to log into a service online. Prominent big tech companies, such as Google and Facebook, use this method through examples such as Google Identity and Facebook Login.
How is email authentication used for log-ins?
Popular websites have different ways of using email authentication to log-in. For example, Gmail uses the OAuth 2.0 protocol and the Google Sign-in to authenticate a Google account and authorize access to user data. In this way, Gmail can be easily used to authenticate people’s information for log-ins. Facebook uses a more complicated set of steps.
Facebook enables users to type their email addresses as usernames rather than make them create their own usernames. They use this method so that its employees can get access to their personal information from their email addresses. This way, they can keep their data to improve the business strategy of these social media platforms. On Facebook, whether someone is signed into Facebook via a computer or an app, the login dialog enables a user to sign into both. If that person is not logged into Facebook, the user will be prompted to login into Facebook and then into its app.
Pros of Email Authentication
There are two major pros about the use of email authentication to log into accounts and applications: it can restrict the amount of information that is needed to log into them and email addresses are relatively simple to recall. Even though it is better to have less information than more to log into accounts and apps, using an email address to log into many websites is not the best idea because spoofing can easily occur online. If companies decide to continue the use of email authentication, people will not be in control of how they are using their data. Consequently, users will lose trust in these companies, and will employ the resources of others.
Cons of Email Authentication
Email authentication facilitates the ability of hackers to access other people’s login credentials when communicating with the authentication platform through spoofing attacks. When the platform’s servers are used effectively in the cloud, their attacks become more effective. Many platforms, such as Facebook, are in agreements with third-party entities that have access to some of your personal data. These entities act as service providers for marketing purposes, analytics for search engines, and to finish payments. So, these platforms and third-party entities use practices that fail to protect user privacy. The negative effects of email authentication should not give users enough incentive to continue utilizing it. However, there are other alternative authentication methods that may be more secure.
What is phone number authentication?
Phone number authentication is an authentication method in which a sender sends an SMS message to a receiver’s phone. Then, the receiver logs into its phone with a one-time code provided in the SMS message. Companies utilize phone number authentication, so that these phone numbers can be sent and kept by Google to enhance their spam and abuse prevention across the Google services, like Firebase. Phone number authentication helps users to easily verify their identities when they are online.
How does it work?
This process is created by a string of numbers on a rotating basis of 30 seconds. Phone number authentication requires the electronic device to produce a six digit code. (The time frame and length of code can vary.) Then, the user can log into an application or account as soon as possible. The more iPhone methods that a company utilizes to enable users to log into their accounts and applications, the safer its digital experience will be. Such iPhone methods include non-text passwords, digital certificates, smart cards that have stored authentication data, and one-time passcodes. When ethical implementation of phone number authentication is executed, people’s privacy is protected.
Pros and Cons of Phone Number Authentication
Phone number authentication is a much more convenient method than other authentication methods because users receive one-time passcodes through text messages. The cell phone acts as a one-time passcode generator that provides users unique codes so that they can log into their accounts and applications. This method only requires a mobile device which most users possess in this day and age.
However, whenever a company utilizes phone number authentication, they make it easier for cybercriminals to gain access to a phone number database. This is significant because users’ phone numbers can be easily transmitted between one another. When people utilize devices with various user profiles, any user that gets SMS messages can log into an account or application with its phone number, thus making it easier for cybercriminals to scam call them.
Phone number authentication is a more secure authentication method than email authentication because it is much easier to learn about an internet user with their email address than their phone number. Yet, phone number authentication requires the memorization of an initial username and password, which can be difficult as most users already have numerous passwords to remember. What if there was a way to verify a user’s identity with the sole usage of a phone number?

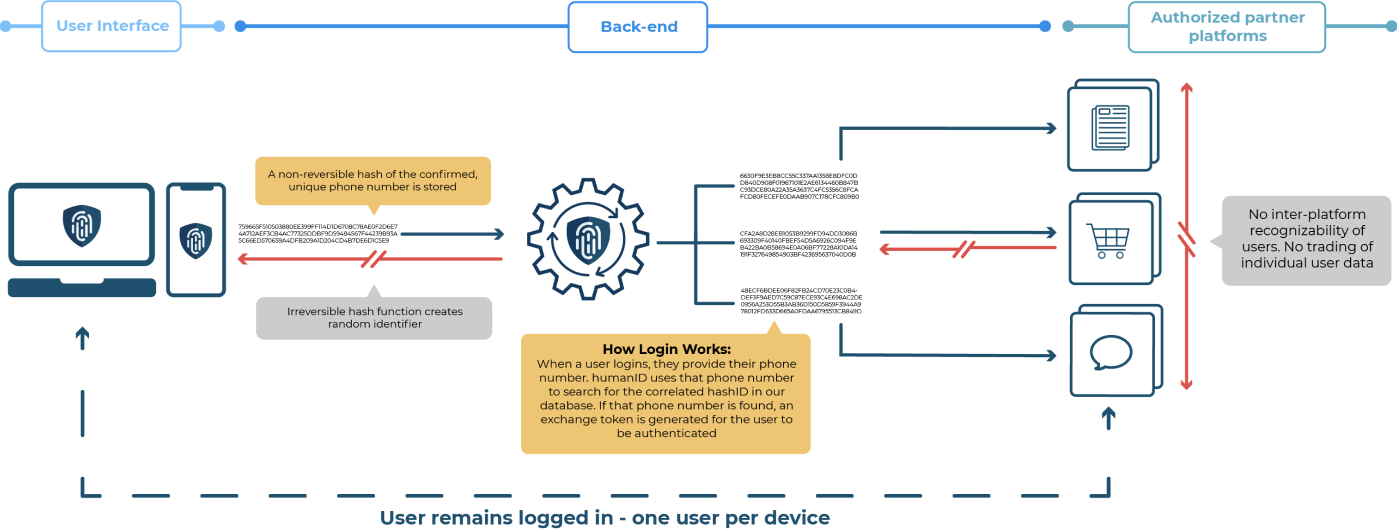
Why use humanID?
humanID is a twist on traditional phone number authentication that ensures heightened security while increasing convenience for the user. humanID is an authentication method that does not store data, has multi-layered protection, and only requires the input of a user’s phone number for verification. A person’s phone number is used momentarily before getting hashed. Each hash serves as a unique identifier to every user-platform connection. When phone number hashing is utilized, a user’s phone number cannot be traced back to the electronic device itself as the original phone number is converted into a string of untraceable letters and numbers. Also, there is no switch of both people’s data or inter-platform identification. Because of those reasons, it is much safer to use humanID’s phone number authentication than it is to use traditional SMS methods or email authentication.
With humanID, there is one person logged into one device. This makes it easy to maintain digital privacy. At humanID, we provide a secure, convenient login experience for our digital users. In this way, we are committed to preserving each person’s privacy. So, why not partner with us?