How To Stop DDoS Attacks
By Said El Hachemy
August 2, 2021
Hackers are always a step ahead of security measures. As data security quality increases, malicious entities create new methods to outperform those security measures. One of the most common attacks on the internet is Distributed Denial of Service (DDoS). Large companies such as Amazon Web Services (AWS), Google, and Github have been victims to DDoS, proving anyone is susceptible. One of the biggest incidents was the Mirai Dyn attack on the Domain Name Server (DNS) service provider Dyn. The DDoS attack successfully rendered the server out of service, making Twitter, SoundCloud, Spotify, Shopify, and other major websites inaccessible. These incidents necesitate businesses to implement ways to mitigate, prevent, and stop these attacks.
What are DDoS attacks?
Denial of service (DoS) attacks occur when a hacker sends a large number of requests to a server to overload it. The server is unable to process the requests and will consequently go offline, thus preventing users from accessing the website. Distributed DoS attacks serve the same purpose. However, instead of sending a large number of requests from a single source machine, the requests are sent from multiple machines. This makes it even harder to determine the source of the attack.
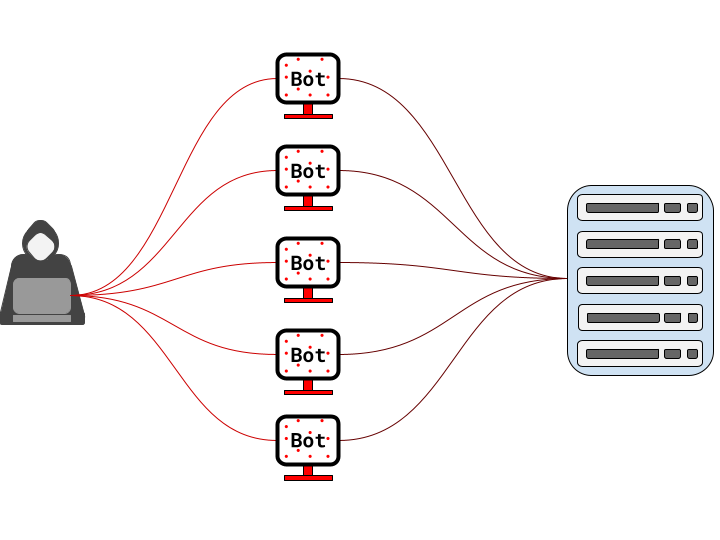
Types of DDoS Attacks
As networking architecture is composed of multiple layers, DDoS attacks can be initiated on any of the layers. Here are some examples of DDoS attacks :
- Ping of death: A ping message is basically a message used to check if the machine on the other end is connected. The recipient usually responds using an echo message. But in case of a DDoS attack, the hacker sends multiple ping messages as fast as possible so that the recipient can’t respond. This consumes the victim’s resources and slows down its responses.
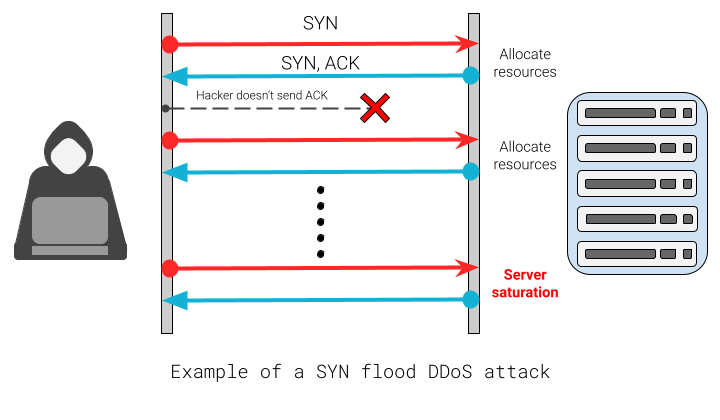
- SYN flood: For two machines to exchange data, a Transport Control Protocol (TCP) connection has to be established. TCP is one of the layers of the networking architecture. A TCP connection is established after exchanging three messages: Synchronization message (SYN) to initiate the connection, synchronization and acknowledgment message (SYN-ACK) to confirm the initiation, and acknowledgment message (ACK) to conclude the establishment. (These messages are also known as the three way handshake.) In a SYN flood attack, the hacker sends multiple SYN messages and never completes the connection establishment. This consumes the victim’s resources and saturates it.
- UDP flood: User Datagram Protocol (UDP) is also one of the networking protocols used to exchange data. But unlike TCP, UDP doesn’t need a connection establishment before exchanging data. Therefore, it is used in applications where data loss is not noticeable, such as video conferencing, voice calls, or streaming. Since each service has its specific port (80 for web services, 21 for file transfer, …), UDP segments are sent to the corresponding ports. A UDP flood attack occurs when a hacker sends a large number of UDP segments to a random port of the victim machine, thus rendering the service corresponding to that port inaccessible.
There are other types of DDoS attacks, but in general, DDoS attacks tend to be successful when they occur in a high rate, large numbers, and a high throughput.
The Risks & Consequences of DDoS Attacks
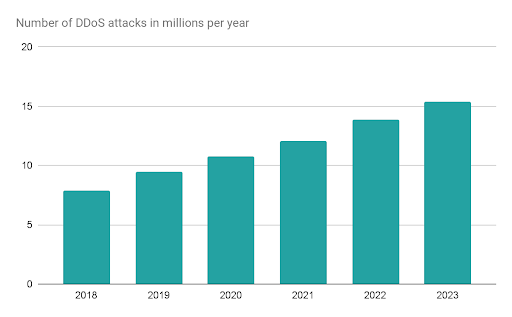
The main goal of DDoS attacks is to make the website slow to respond to a user’s request, or to put it completely out of service. An attack could last for days, rendering vital services including banks, cloud services, authentication services, and others, offline. This threatens businesses, and can potentially cost them millions of dollars during an attack. The simplicity of this attack has a major role in the increase of its frequency and magnitude. As stated in the Cisco annual internet report 2018-2023, the number of attacks is always on the increase, and will reach up to 15.4 million attacks by 2023.
How to Stop DDoS Attacks
There exist multiple ways to stop DDoS attacks. For example, businesses could use detection mechanisms to determine if they are attacked or not, and then take the appropriate measures to handle the attack. Another approach is to prevent the attack from occurring in the first place. Among the popular ways to mitigate this attack, is the use of:
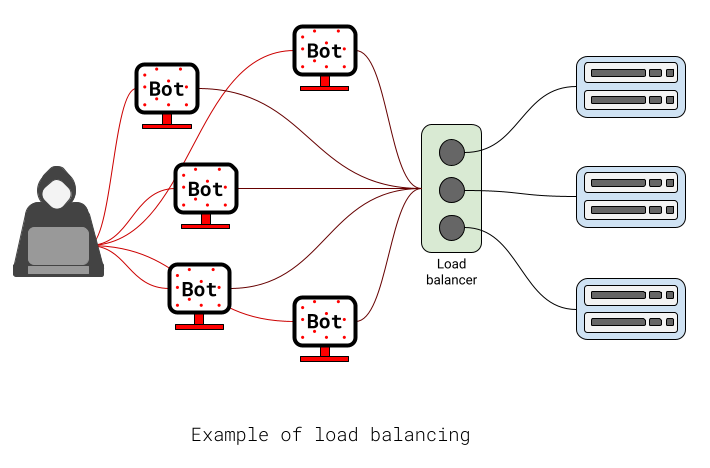
- Load balancers. These are devices that reroute traffic to other servers to reduce the load off the main server.
- Firewalls. These can be installed in almost every networking device (computer, router, etc.), and have rules that inspect and decide whether a packet is malicious or not.
- Intrusion Prevention System (IPS). A system that inspect packets to stop malicious software from exploiting vulnerabilities.
Although recently, some of these mechanisms may have a hard time keeping up with DDoS attacks, due to the limited capabilities of these mechanisms to inspect every packet at a high rate, especially when bigger DDoS attacks are occurring at a speed of terabytes per second. For that reason, businesses such as Cloudflare, Fastly, Imperva were created to specialize in security protection and attack mitigation. These businesses offer many services, including attack notification, network monitoring, attack analysis.
Other methods of DDoS mitigation can be related to user authentication, since traffic can’t get access to servers if it wasn’t proven to have come from legitimate users. One way of doing this is by using CAPTCHA. This has the potential to stop the attack, but also has the downside of risking user privacy. Hence the need for an alternative that could protect user privacy while being fast, simple to use, and easy to implement. Such an alternative is humanID. On top of satisfying the previous requirements, we are also a non-profit organization, with the sole purpose of granting users a safe and private access to any service. Since humanID is bot-resistant, it has the ability to detect if a request came from a real person or a bot. This is done by checking for human-like behavior while receiving authentication requests. humanID works using hashed phone numbers as credentials to identify users, and this hashing process ensures that a user’s information is irretraceable. As security measures increase, attacks are becoming increasingly dangerous and smart, which calls for better ways to protect users and services alike.


